Stay updated with the latest cybersecurity news!
Cybersecurity Newsletter
April 10, 2024
In This Edition:
- [News] Is NIST’s Updated Cybersecurity Framework a Silver Bullet? Experts Weigh in: First published in 2014, the NIST Cybersecurity Framework (NIST CSF) provides organizations with guidelines and best practices for managing cyber risks and compliance. Although the framework is mandatory only for U.S. federal agencies, businesses aiming to engage with the government as contractors, partners, or vendors will likely be required to comply with its standards.
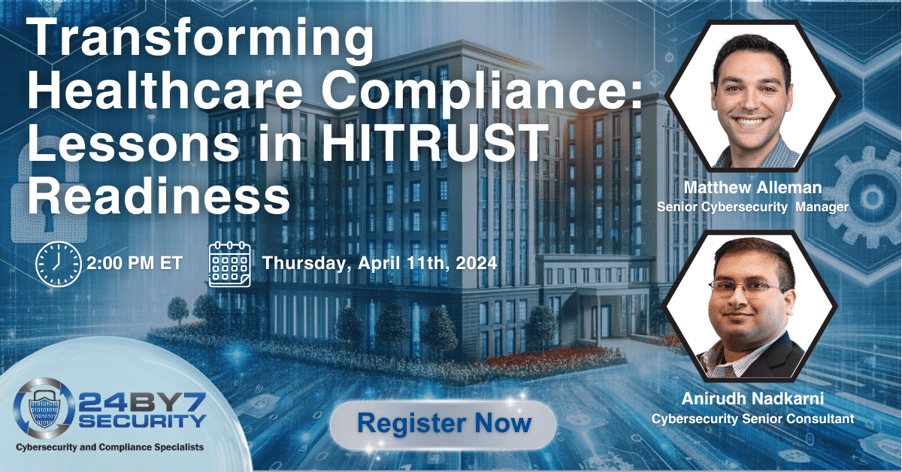
- [Event] Transforming Healthcare Compliance: Lessons in HITRUST Readiness: Join us for an insightful webinar as we delve into the heart of healthcare compliance with a special focus on the HITRUST CSF. This session will offer a comprehensive exploration of how HITRUST CSF serves as a beacon for healthcare organizations navigating the complex landscape of security standards and regulations. Our discussion will highlight how HITRUST CSF seamlessly integrates diverse regulatory requirements, industry standards, and frameworks, providing a robust yet flexible foundation for managing the unique risks inherent in healthcare operations.
- [Event] Serious Business: PCI DSS 4.0 Compliance After April 1st: Join us for an exclusive, conversational webinar, "Serious Business: PCI DSS 4.0 Compliance After April 1st." Complying with PCI DSS 4.0 truly is “serious business.” In fact, not being compliant with PCI DSS 4.0 (which is the mandated standard beginning April 1st, 2024) has major consequences. Non-compliance can result in losing your ability to accept credit cards, monthly fines, and liability for fraudulent charges, or even having to close your business. PCI DSS 4.0 has brought significant changes, presenting new challenges and opportunities for businesses worldwide. Now, it's crucial to understand what lies ahead in this evolving regulatory environment.
- [News] Advanced cybersecurity performance translates to higher shareholder returns: Highly regulated industries like healthcare delivered a 372% higher shareholder return compared to their peers, further highlighting the organization-wide importance of cybersecurity.
- [Blog] How Vulnerability Assessments Strengthen Security: The process of vulnerability assessment is an in-depth evaluation of an organization's cybersecurity infrastructure, which includes networks, systems, hardware, software, and other information technology. The purpose is to identify vulnerabilities in these areas in order to prioritize and remediate them. Remediation prevents cybercriminals from exploiting an organization’s weaknesses to steal sensitive data and other digital assets.
Is NIST’s Updated Cybersecurity Framework a Silver Bullet? Experts Weigh in
First published in 2014, the NIST Cybersecurity Framework (NIST CSF) provides organizations with guidelines and best practices for managing cyber risks and compliance. Although the framework is mandatory only for U.S. federal agencies, businesses aiming to engage with the government as contractors, partners, or vendors will likely be required to comply with its standards.
Hear from the Experts

Transforming Healthcare Compliance: Lessons in HITRUST Readiness
Join us for an insightful webinar as we delve into the heart of healthcare compliance with a special focus on the HITRUST CSF. This session will offer a comprehensive exploration of how HITRUST CSF serves as a beacon for healthcare organizations navigating the complex landscape of security standards and regulations. Our discussion will highlight how HITRUST CSF seamlessly integrates diverse regulatory requirements, industry standards, and frameworks, providing a robust yet flexible foundation for managing the unique risks inherent in healthcare operations.
Sign up today!

Serious Business: PCI DSS 4.0 Compliance After April 1st
Join us for an exclusive, conversational webinar, "Serious Business: PCI DSS 4.0 Compliance After April 1st." Complying with PCI DSS 4.0 truly is “serious business.” In fact, not being compliant with PCI DSS 4.0 (which is the mandated standard beginning April 1st, 2024) has major consequences. Non-compliance can result in losing your ability to accept credit cards, monthly fines, and liability for fraudulent charges, or even having to close your business. PCI DSS 4.0 has brought significant changes, presenting new challenges and opportunities for businesses worldwide. Now, it's crucial to understand what lies ahead in this evolving regulatory environment.
Secure your spot!

PCI DSS 4.0 Checklist
Do you know what to do to comply with PCI DSS? Data security and compliance are important responsibilities that IT professionals oversee. However, it's easy to mix up the different recurring tasks needed to be compliant.
How Vulnerability Assessments Strengthen Security
The process of vulnerability assessment is an in-depth evaluation of an organization's cybersecurity infrastructure, which includes networks, systems, hardware, software, and other information technology. The purpose is to identify vulnerabilities in these areas in order to prioritize and remediate them. Remediation prevents cybercriminals from exploiting an organization’s weaknesses to steal sensitive data and other digital assets.
Read More

24By7Security, Inc. is a full-service Cybersecurity strategy, implementation, operations, and training firm. We provide Cybersecurity and Compliance related services across all functions of the enterprise. Our Cybersecurity services include security risk assessments, vulnerability assessments and penetration testing, social engineering testing, web application testing, policies and procedures, incident response management, forensics, cybersecurity awareness training, Virtual CISO Services, and more. Our Compliance services include CMMC Readiness, HITRUST Readiness, CFPB/DFA, FIPA, FERPA, SOC-SSAE 18, GLBA, HIPAA, PCI, SOX, GDPR, ISO 27001, FFIEC, NIST-CSF, NYDFS Cybersecurity Regulations, and others.


.png?width=900&height=471&name=PCI%20%204-18-24%20webinar%20%20(2).png)

