
As of Nov 2021, CMMC 2.0 was introduced and the information below may not apply in its entirety.
According to the Office of the Under Secretary of Defense for Acquisition & Sustainment, CMMC is described as the following:
"CMMC stands for "Cybersecurity Maturity Model Certification." The CMMC will encompass multiple maturity levels that range from "Basic Cybersecurity Hygiene" to "Advanced/Progressive." The intent is to incorporate CMMC into Defense Federal Acquisition Regulation Supplement (DFARS) and use it as a requirement for contract award."
Stepping back a moment from this very brief but very digestible understanding of CMMC, we will elaborate more in-depth the purpose and effects CMMC will bring.
The Cybersecurity Maturity Model Certification (CMMC) has been launched by the Department of Defense (DoD) as a required certification for most contract awards to vendors or suppliers. The supply chain to the DoD includes over 300,000 companies and is called the Defense Industrial Base (DIB). The CMMC is a consolidated standard for implementing cybersecurity across this defense industrial base. This certification is the action that the DoD is taking to protect sensitive defense information located on vendors' information systems.
CMMC Version 1.0 was released on January 30th, 2020. Version 1.02 was released on March 18th, 2020. DIB and DoD stakeholders provided input to creating the CMMC model. The model includes maturity processes and cybersecurity best practices from various cybersecurity standards, frameworks, and other references.
Before requiring CMMC as a certification for its vendors, the DoD required that its contractors self-assess and attest to compliance with NIST 800-171. With the CMMC, the compliance requirement becomes more robust as compliance is verified, audited, and certified by a third-party certification organization. The CMMC thus addresses the shortcomings of self-assessment and also enforces controls to protect sensitive data classified as Federal Contract Information (FCI) or Controlled Unclassified Information (CUI).

To learn more about FCI and CUI, and about who needs to comply with CMMC, read our blog: Who needs to comply with CMMC?
The CMMC is the next step of the Department of Defense (Dod) to enforce and improve the depth and breadth of cybersecurity protections for relevant data following the Defense Federal Acquisition Regulation Supplement (DFARS) issued in 2016.
In the past, contractors were responsible for implementing, monitoring, and certifying the security of their IT systems and any confidential DoD information stored on those devices. Contractors, however, remained responsible for performing critical cybersecurity requirements. The CMMC changes this model by requiring third-party assessments of contractors' compliance with specific practices and capabilities that can adapt to all brand new and ever-evolving cyber threats. As a key tenet of cybersecurity reminds us to always "Trust, but Verify", CMMC seeks to fulfill the verification task through third party certification.
In other words, the CMMC will create a program to verify that a DoD contractor has put in place sufficient cybersecurity controls and processes to actively protect controlled unclassified information (CUI) that resides on DoD and DoD contractors' networks.
Even the Chief Information Security Officer for Assistant Secretary for Defense Acquisition, Katie Arrington, has said, 'WWI & II changed warfare with trenches, and to defeat the trench the tank was invented. Cyberwarfare is the "new trench," cybersecurity is the tank, and CMMC is the tank's tracks.'
The most obvious impact will be re-engagement. Every contractor's work will be at risk if they are not certified at the minimum level required for their contract at the time the deal comes up for rebidding or renewal. It will, therefore, be advantageous to begin asking about the intended CMMC requirement during the RFI or as soon as possible during the entire process.
With this certification, there are potential advantages of winning new business if your company receives a higher CMMC level than your competition.
Another significant positive to the new certification will be the elimination of ambiguity. The industry has mainly struggled to grasp compliance and understand how the DoD would enforce compliance.
DFARS clause 252.204-7012 stipulates that a company with possession of CUI must self-assess its cybersecurity posture and self-attest that it complies with all security controls of NIST 800-171. The main difference between NIST 800-171 and CMMC is that self-attestation will no longer suffice.
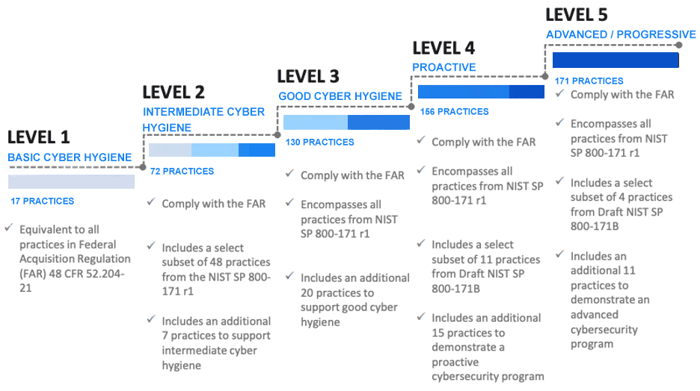
The other differences are that CMMC has the five levels of maturity which are not present as part of NIST 800-171. CMMC has a total of 171 requirements spread out over its five levels, while NIST 800-171 has 110 requirements. Level 1 CMMC certification requires compliance with 17 NIST 800-171 requirements. A company seeking CMMC Level 3 certification will have to comply with all 110 requirements of NIST 800-171 plus 20 other practices. At the most advanced Level 5, CMMC requires organizations to comply with all 110 NIST 800-171 requirements plus 61 different practices.
CMMC, therefore, is more comprehensive than NIST 800-171, and we dare say, also more pragmatic, as it varies the complexity and burden of compliance based on access to sensitive data.
For the next few years, CMMC and NIST 800-171 mandates on defense contracts will exist in parallel, until all contracts with the DoD start requiring CMMC. Members of the Defense Industrial Base (DIB) should, therefore, be familiar with both NIST 800-171 and CMMC.
As NIST 800-171 requirements form a large part of the CMMC capabilities and controls, DoD prime contractors and sub-prime contractors who have proactively addressed NIST 800-171 will find that their challenge in migrating to CMMC will be reduced. The better their compliance with NIST 800-171, the higher their CMMC certification is likely to be.
DoD contractors should prioritize understanding all of the CMMC's technical requirements. Besides, DoD contractors must prepare not only for certification but for long-term cybersecurity flexibility. Steps on how all of the CMMC assessments will be carried out and how to challenge those assessments are anticipated in the near future. DoD contractors who have already begun to position themselves better will need to evaluate their procedures, practices, and gaps. With this entire process done, this will meet CMMC's mandatory contract requirements for future assessment.
If you would like to know where contractors can keep up to date on the certification process, there currently is a CMMC FAQ that the Office of the Under Secretary of Defense for Acquisition & Sustainment maintains.
We also have written some information that you can access that explains everything we talked about in greater detail. You can read about it here!
To start, control families are now called Domains. Domains include various Capabilities, which in turn, consist of Practices and Processes. CMMC requirements are broken down by Domains and Capabilities, and then each Practice and Process within them is assigned to a level.
That being said, CMMC is formatted as a hierarchical matrix. At the highest level, there are 18 different "domains." These domains are considered key cybersecurity areas. For a given domain, there are "processes" that span a subset of five levels. Also, for a given domain, there are either one or more "capabilities" that span a subset of five levels. Finally, for a given "capability," there are one or more "practices" that span a subset of five levels.
A large majority of the Domains use the same terminology and detail the same best practices as described in NIST Special Publication (SP) 800-171.
The CMMC is comprised of 17 domains and 171 practices.
The domains can be broken down into 43 capabilities, with only particular capabilities required for each level. DoD Contractors that are looking to reach Level 5 certification must comply with all 171 practices. Practices are listed against a capability and described within each domain, for each of the levels.
The full list of Domains and Capabilities are shown in this interactive infographic!
The CMMC framework contains five levels ranging from basic hygiene controls to state-of-the-art controls, but unlike NIST 800-171, the CMMC will not provide a self-assessment component. Every DoD Contractor that plans to conduct business with the Department of Defense will be required to partake in an audit by an authorized auditing entity before bidding on a contract.
As of the 1.0 release, here is a Level by Level breakdown of the requirements going beyond or outside NIST 800-171.
As we know, CMMC primarily leans on NIST 800-171; however, many frameworks are being considered and integrated for the new Cybersecurity Maturity Model (CMM). NIST 800-53, FedRAMP, CMMI, SANS, FIPS 140-2, RMF, ISO 9000, and others are influencing the new model. Other federal agencies, industries (the financial sector, for example), and industry experts will be consulted for lessons learned.
As previously mentioned, the CMMC establishes five certification levels that reflect the maturity and reliability of a company's cybersecurity infrastructure to safeguard sensitive government information on contractors' information systems.
The five levels are tiered and build upon each other's technical requirements. Each level requires compliance with the lower-level requirements and institutionalization of new processes to implement specific cybersecurity-based practices.
This diagram provides a better look at what the five levels are and what is required to move up a level. To get a better and more in-depth analysis of each of these levels, we have an entire blog dedicated to that information!
The road to becoming CMMC accredited can be a lengthy path. Still, it can be made less challenging by understanding the layout of the framework and the requirements of each specific security level. Organizations that are looking to conduct business with and bid on DoD contracts need to ensure that their cybersecurity controls are aligned with the particular level of certification they are attempting to obtain.
An excellent first step to begin is to perform a gap assessment to understand your current state of affairs, and then implement an improvement plan. 24By7Security has performed many gap assessments for industries needing to comply with regulations.
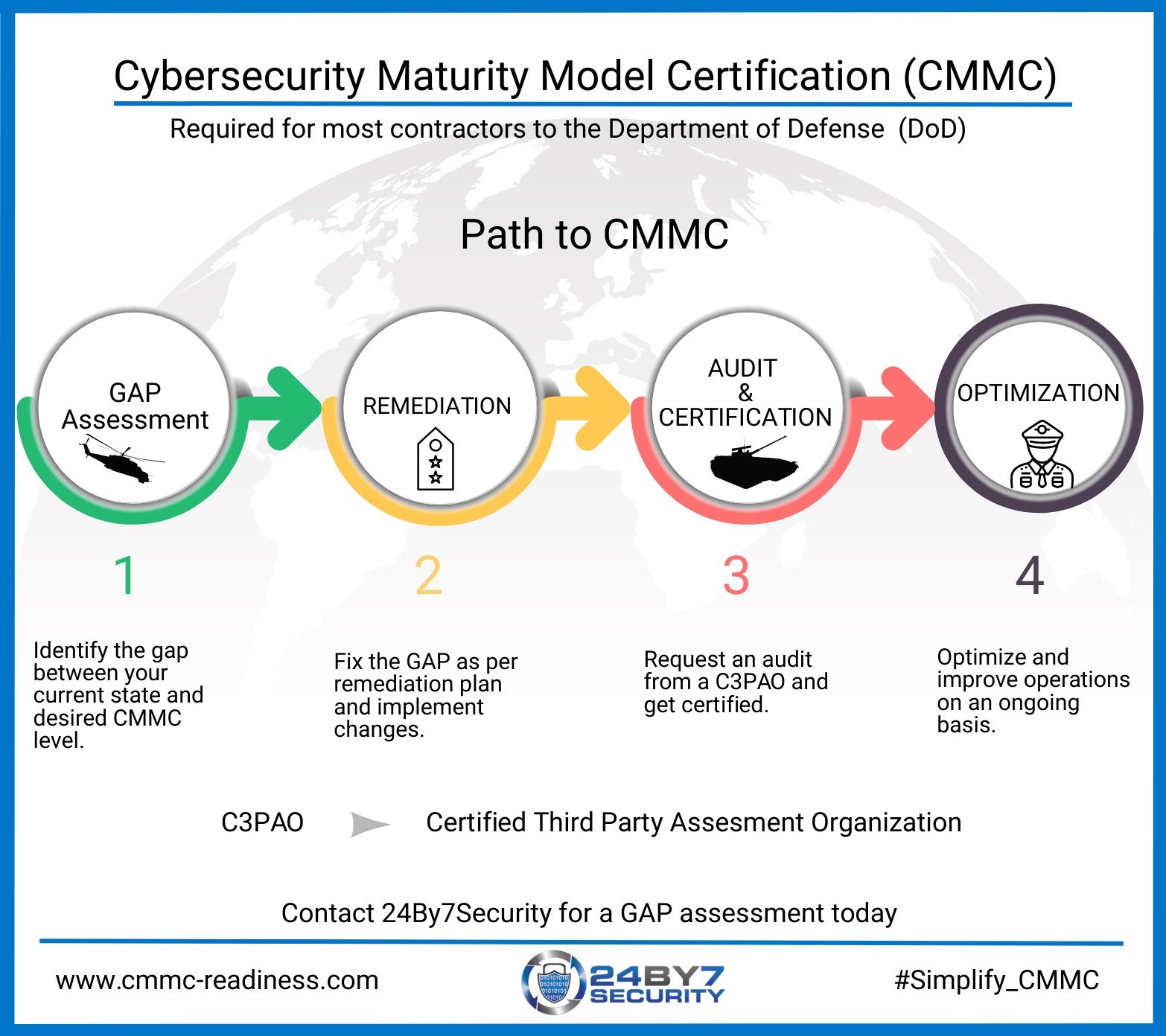
The four phases in the path to certification break down into ten logical steps, as described below. For your ease of access, here are the ten steps for an organization seeking certification at a CMMC level:
24By7Security can help you get ready for CMMC cost-effectively and efficiently that’s reliable and trustworthy. Schedule a call with us today!
%20Combo%20Graphic%20Horizontal.png?width=600&name=RP(O)%20Combo%20Graphic%20Horizontal.png)
At 24By7Security, Inc. we are your trusted partner in Cybersecurity and compliance. We help you manage your cyber risk programs so that you can focus on your business.
24By7Security, Inc.
4613 N. University Drive, Suite #267
Coral Springs, FL 33067
Toll Free: (844) 55-CYBER
Email: contact@24by7security.com
© 2019 24By7Security, Inc. - (844) 55-CYBER. All Rights Reserved.
Signup for news and special offers!