Security Risk Assessment Services
Connecting to the Internet has delivered countless, amazing benefits to organizations as well as individual consumers. However, if not managed and secured properly, this connection can disclose proprietary information to the outside world. Having such information fall into the wrong hands poses a significant risk to any organization.
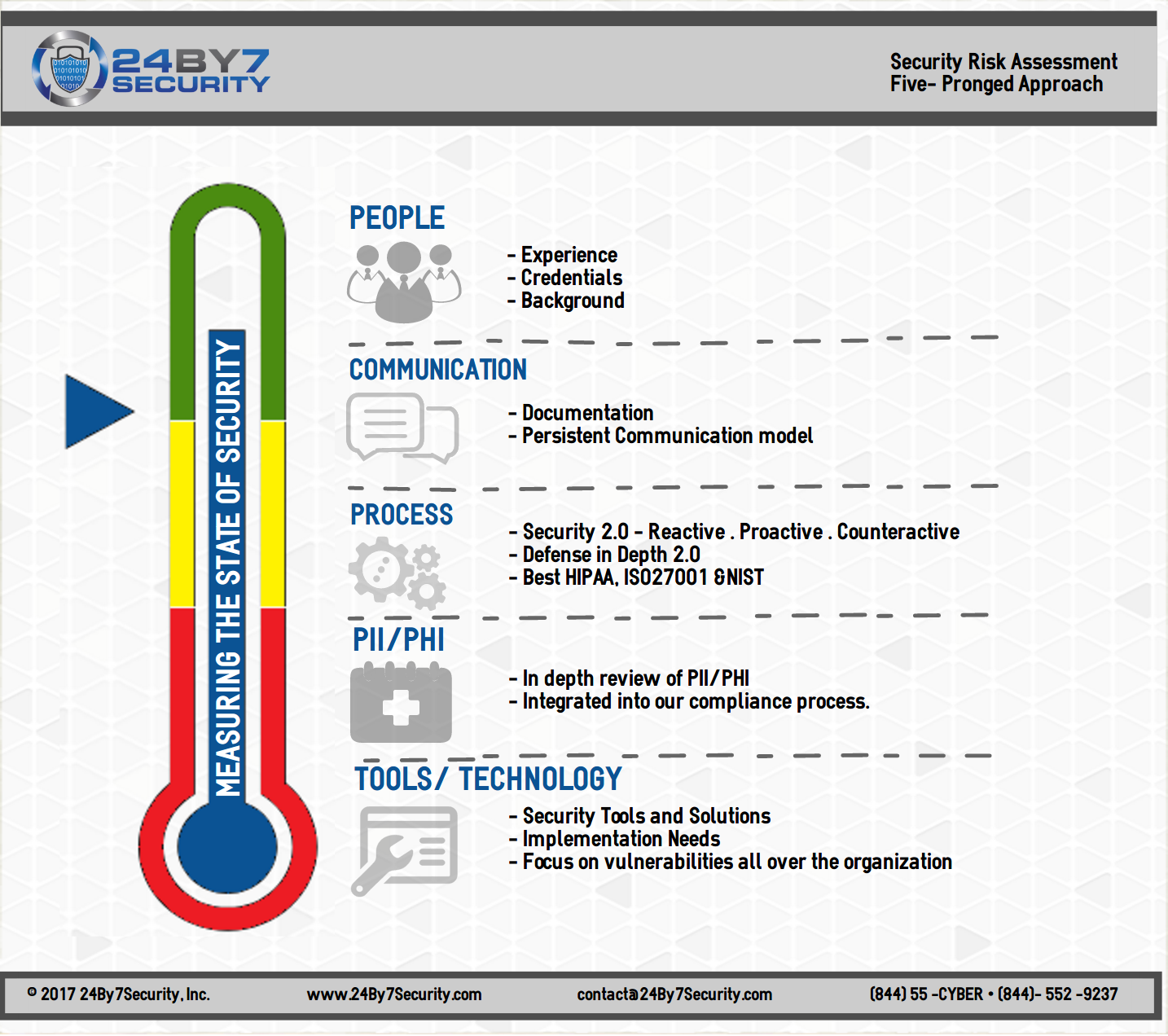
Understanding the current cybersecurity posture of an organization is a vital first step in strengthening that posture and resolving security weaknesses. The accepted best practice and surest way to acquire this understanding is to conduct a security risk assessment.
Many regulations require a security risk assessment as a matter of compliance. These include ISO/IEC 27001, governing information security management systems, as well as the NIST cybersecurity framework, Sarbanes-Oxley Act, and the GLBA. In addition, the HIPAA Security Rule, the ONC and CMS Rules known officially as the 21st Century Cures Act, and the CMS Interoperability and Patient Access rule governing the security of healthcare information require routine security risk assessments.
Many company policies require enterprise-wide security risk assessments to be conducted at least annually, or upon any major change to infrastructure or processes. We recommend annual security risk assessments as a best practice and typically work with an organization's CISO or VCISO to schedule and conduct the security risk assessment as part of an overall cybersecurity program.
A security risk assessment identifies the organization's assets (laptops, desktops, servers, network, and other security devices), risks associated with the assets, mechanisms the company has in place to manage those risks, and how those mechanisms are documented and managed. The risk assessment provides a complete picture of the overall risks and recommendations for addressing them.
Download Our Security Risk Assessment Spotlight Flyer
Our Security Risk Assessment Services
- Adherence to NIST SP 800-30 nine-step Risk Assessment Methodology
- Penetration Testing and Vulnerability Assessments (Assets) - External and Internal
- Penetration Testing (Web Applications)
- Social Engineering Testing (Physical, Vishing, Phishing)
- Business Associate and Third-Party Vendor Risk Assessments
- Asset Management
- Medical Device Risk Assessments
- Development of Remediation Plan and Implementation of Remediation Measures
- Development of Policies and Procedures for Cybersecurity and Compliance Requirements

The Challenges of Do-It-Yourself Security
Internet connectivity comes at a price. Intellectual property, data, and other business assets can be inadvertently exposed to unauthorized parties, or can be leaked maliciously. Having your data in the wrong hands poses a significant but unnecessary risk.
- Do you know if your data is safe from both external and internal threats?
- Do you know if your IP, payroll and personnel data, financial information, and strategic plans are secure?
- Are you certain you are in compliance with regulatory requirements and best security practices?
Schedule a Call


