The year 2019 set a record for data breaches. According to the resource site HelpNetSecurity.com, the total number of data breaches rose 33% in 2019 over 2018, with medical services, retailers, and public entities being affected to the greatest extent.
A data breach, in its simplest terms, is the exposure of individuals’ personal information to the risk of abuse. Or, as cnet.com/news more colorfully describes it, “leaving sensitive customer data unprotected in the open wilds of the internet, to be bought and sold by hackers who barely(have)to lift a finger to find it.”
In fact, many of us are enjoying our third or fourth years of free credit monitoring service, compliments of various high-profile companies who have suffered data breaches affecting our personal information. This service is a way of atoning for their vulnerable security programs and attempting to repair our shaken confidence and their own tarnished images.
Despite the repeated occurrence of data breaches year after year, we have little choice but to trust the companies we do business with—from the global giant, to the area hospital, to the corner retailer—who use and store our personal and financial data.
In today’s hyper-connected cyberspace, data breaches are inevitable. However, there are measures every business can take to reduce risk and strengthen security. The essential first step is to understand where your vulnerabilities are, and this is why every business must conduct a thorough assessment of their security risks—at least once!
Among the cyber threats wreaking havoc around the world, ransomware, phishing, data leakage, hacking, and insider actions continue to top the list. Many of the business tools we use, including email, social media, and IoT devices, can introduce these threats as well as other risks.
Of course, certain industries are vulnerable to specific cyber threats, often due to the nature of the data they acquire, use and store. For this reason, the financial services and healthcare industries are especially vulnerable, despite heavy regulation.
The financial services industry is highly regulated, and yet incurs roughly 35% of all data breaches each year. Topping the list of cyber threats in this industry, according to a 2019 article in Forbes, are web application attacks, distributed denial of service (DDOS) attacks, and insider threats. Web applications, including business-critical applications hosted online, are vulnerable to buffer overflow and SQL injection attacks, to name a few. DDOS attacks cause websites and web applications, such as customer self service sites, to slow down significantly or even fail. And insider threats are particularly concerning for banks, insurance companies and other providers of financial services. Disgruntled employees may collude with criminals to steal data—and even money.
The healthcare industry is also plagued by data breaches despite extensive regulation by HIPAA and the HITECH Act. Interestingly, where the cost of a data breach, per individual record, is $206 in the financial services industry, in healthcare that cost is $408 per record—virtually double. Top threats in the healthcare industry include the challenges of cloud security, unsecured mobile devices, IoT devices, ransomware, and people.
Healthcare organizations increasingly move large volumes of sensitive data to the cloud, relying on IT staff to manage and secure it. “Smart” healthcare devices that can be implanted or worn (such as pacemakers and insulin pumps) are connected to systems and vulnerable to hacking. The inadequacy of employee security training, a serious threat to healthcare data, creates vulnerabilities to ransomware, phishing,email scams and other social engineering exploits.
Security threats can be defined in four broad categories, based on Intention and Origination. These categories are:
 Phishing and ransomware, for example, are external threats with malicious intentions, as is most hacking. Data leakage is generally an internal threat without malicious intent, although there are documented cases of employees deliberately creating data leaks.
Phishing and ransomware, for example, are external threats with malicious intentions, as is most hacking. Data leakage is generally an internal threat without malicious intent, although there are documented cases of employees deliberately creating data leaks.
When assessing the security risks in any organization, regardless of industry, these four threat categories help assessors to prioritize the level of risk and potential for harm, and aid in guiding remediation actions.
We have said that every organization must conduct a Security Risk Assessment at least once. The examples above should help clarify why it is so important not only to have a baseline assessment of your security posture but also regular assessments thereafter—if not for you, then for your customers, clients, patients and other stakeholders.
Security threats can be categorized at three levels, from Low to Medium to High, a triage system that enables risks identified during the assessment to be prioritized for remediation.
The three levels can be considered in terms of their impact on the organization and its assets, and are generally described as follows:
In its simplest terms, a Security Risk Assessment is a formalized, methodical evaluation process that produces an actionable report of findings. The assessment consists of identifying the organization’s IT assets and the risks or vulnerabilities associated with those assets, including computers (tablets,laptops, desktops and smartphones), servers, networks, storage devices, security devices and other connected devices. Vulnerabilities may be due to misconfiguration, outdated software, unsupported software and hardware,and other issues.
The security assessment also evaluates mechanisms the organization employs to manage the risks associated with its IT assets, as well as how those mechanisms are documented and managed. In addition, the assessment reviews risks created by weak, incomplete, or non-existent policies, procedures, personnel, technology, and security strategy.
A comprehensive Security Risk Assessment will also view the organization’s network(s) from outside, as a hacker would, with attempts to penetrate the network(s) in order to access company data.This process includes scanning all company IP addresses to identify security vulnerabilities that could be exploited by hackers.
In addition, a thorough Security Risk Assessment incorporates social engineering testing to ascertain vulnerabilities to phishing schemes and similar socially engineered exploits. This document itemizes the various tests that are included in a professional Security Risk Assessment.
Step 1 entails identifying the scope of the particular risk assessment to be conducted. This may be stated in terms of systems, databases, platforms, and operations related to the type of information created, received, maintained or transmitted by the organization, and the security and compliance regulations that apply. It is important to define the scope first in order to avoid subsequent oversights.
Step 2 identifies and documents where the pertinent data and information are stored, received, maintained, and transmitted,which may be accomplished by conducting interviews and operational walk-throughs. It may also involve reviews of policies and procedures, network diagrams, relevant software and applications, previous assessment report and other pertinent resources.
Step 3 involves identifying and documenting threats and vulnerabilities. It may begin with developing a list of potential threat sources. It also entails developing a list of system vulnerabilities that could be exploited by the potential threat sources.
Step 4 entails assessing and documenting the security measures and controls that are currently in place to safeguard the pertinent data and information, including security of the systems, software and other tools touching that data. This is the final activity involved in gathering, organizing and evaluating information.
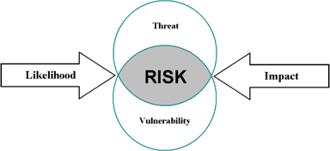 Risk can be defined as the intersection of a threat and vulnerability, influenced by likelihood and impact,as illustrated in the chart at right.
Risk can be defined as the intersection of a threat and vulnerability, influenced by likelihood and impact,as illustrated in the chart at right.
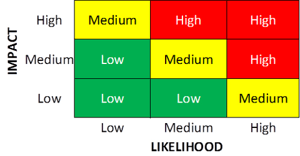
Steps 5, 6 and 7 involve determining the likelihood of the occurrence of the various threats identified (see Step 3), the potential impact of each threat should it occur, and the assignment of a value to each risk. The matrix below illustrates this intersection and indicates severity ratings.
 The activities required in these steps are complex and multi-dimensional. The importance of applying extensive experience in conducting risk and threat assessments, in conjunction with expert analytical capabilities, cannot be overstated.
The activities required in these steps are complex and multi-dimensional. The importance of applying extensive experience in conducting risk and threat assessments, in conjunction with expert analytical capabilities, cannot be overstated.
Step 8 entails finalizing documentation for the risk assessment—a vital step in completing the assessment. Documentation generally consists of a Summary Report and a Detailed Report. Back-up documentation will include various mechanical and electronic test results, which are generally extensive and difficult for the non-technical reader to decipher but which comprise an integral part of the foundation of the assessment, along with the materials outlined in Step 2.
One of the most important elements of the Detailed Report is a description of the corrective actions that should be taken to remediate risks determined to be at the high and moderate levels (see Step 2d). Implicit in the commissioning of any risk assessment is the desire to identify risks in order to address or mitigate them and, in doing so, better protect the security and privacy of the organization’s client, customer, patient, employee, and other stakeholder information.
A transcending benefit of Step 9, which constitutes follow-up assessment, is in demonstrating that identified risks have been remediated, effectively closing the loop for those risks. It also provides an impetus for updating systems, software, applications, and company policies and procedures, and employee training, all of which contribute to enhanced security. In a robust security program, follow-up assessments may be conducted annually, bi-annually, or on some other schedule determined by the organization based on available budget, manpower and other resources.
There are two approaches to conducting a Security Risk Assessment. One is to do it yourself. The other is to outsource it.
Large companies with a knowledgeable, experienced IT team in-house might be tempted to engage them to conduct the assessment. This do-it-yourself approach may provide the advantage of saving money, since most of the expense is already baked in as overhead. However, this strategy risks delaying the assessment as staff are pulled away on other priorities (which, of course J, never happens in IT!), and threatens objectivity in the identification and reporting of security gaps. It’s a bit like having the fox guard the hen house, because insider threats pose a significant risk to a company’s data, systems, and reputation.(See Section 2c–Threat Categories)
A better way to conduct your Security Risk Assessment is to hire a credentialed security professional with proven experience in conducting compliant Security Risk Assessments and delivering compliant, actionable reports. There are many security firms available for this purpose, including 24By7Security.
The number and identities of the parties involved in a risk assessment depend to a great extent on the size of the organization for whom the assessment will be conducted, the industry it is part of and the vulnerability and regulatory scope of that industry.
For any organization, however, it is an accepted truth that security must be addressed by all levels, including executive leadership, business unit managers, IT staff, and third-party service providers who work within the organization and its information systems.
For a large enterprise, high-level engagement could be required of the CISO, CIO and/or CTO, while more active participation would be required of key function managers, such as those in system development, software development, various operating platforms, network engineering and network security. Based on the corporate culture, it could be necessary to engage HR. In any case, the team conducting the assessment should be clearly identified in the interest of full access and cooperation as well as accountability, especially if the assessment is to be conducted in-house.
In smaller organizations, including healthcare practices or financial services providers for whom data security and privacy are highly regulated, the required parties might be limited to an external risk assessor and the organization’s CEO, IT manager and/or office manager, for example. External parties, such as Business Associates in the healthcare industry, may also be engaged via interview, survey, and/or review of interfacing systems.
It is important, also, to understand that the real work begins upon completion of the risk assessment, when it is necessary to create a Mitigation Action Plan (MAP) the organization can follow to implement the security recommendations and thereby remediate risks. In a larger enterprise, this generally falls to members of the IT team. In a smaller organization, where resources may be limited, the risk assessor is frequently engaged to develop the MAP and, in many cases,may also be engaged in its implementation.
At a minimum, any qualified firm should have evidence that they have conducted numerous Security Risk Assessments and continue to do so. They should be willing to share a few sample reports, with all identifying information redacted, to demonstrate the scope of their assessment work. They should also be able to provide references who can confirm the quality and timeliness of their work.
The individual(s) conducting the assessment should have evidence of current credentials required for assessments. The best certifications include those like Certified Information Security Systems Professional (CISSP), Certified Information Systems Auditor (CISA) and Certified Ethical Hacker (CEH). It is also useful to have Certified Information Security Manager (CISM) and Certified in Risk and Information Systems Control (CRISC)credentials
Specific to a HIPAA Security Risk Assessment for healthcare industry members, additional credentials should also include those like Health Care Information Security and Privacy Practitioner (HCISSP), because the requirements of the HIPAA and HITECH acts are very specific to healthcare records and information, including electronic health records(EHR).
Ask for a proposal for the Security Risk Assessment so that you can review in detail the scope, methodology and deliverables. It will also help you confirm that the proposed assessment meets the requirements of the regulations specific to your industry and business.
There are a few different types of assessments based on their focus. Most often, the type of Security Risk Assessment applicable to an organization has to do with the industry (or industries) in which the organization operates, and the regulations governing that industry. Some examples include the education, credit card payment, financial services, and healthcare industries. These industries have well established regulatory requirements and governance, as outlined below.

The Security Risk Assessment is a flagship service of 24By7Security, and we have developed various types of assessments in order to meet the requirements of these and other governing regulations.
The standards promulgated by ISO 27001 guide an organization in managing the security of assets such as financial information, intellectual property, employee data, or information entrusted to it by third parties. This is the best-known standard in the family providing requirements for information security management systems (ISMS). It is important to note that ISO 27001 guidelines may apply to virtually any industry, in similar fashion to the guidelines of the Sarbanes-Oxley Act with respect to public companies.
Educational institutions are required to comply with the Family Educational Rights and Privacy Act (FERPA), a federal law that protects the privacy of student education records. In addition, educational institutions involved in medical instruction and practice must comply with HIPAA as well. Educational institutions that accept payments via credit card for services such as tuition, campus store purchases, athletic event fees and other purchases, must also comply with Payment Card Industry requirements.
 The Payment Card Industry Data Security Standard (PCI DSS) applies to organizations of any size that accept credit card payments. If your company stores, processes, and/or transmits cardholder data, you are obligated to ensure that data is stored securely and in compliance with this standard. One way to accomplish this is by using a PCI-compliant hosting provider to securely host your cardholder data.
The Payment Card Industry Data Security Standard (PCI DSS) applies to organizations of any size that accept credit card payments. If your company stores, processes, and/or transmits cardholder data, you are obligated to ensure that data is stored securely and in compliance with this standard. One way to accomplish this is by using a PCI-compliant hosting provider to securely host your cardholder data.
Any business or entity subject to the PCI Data Security Standard should have a current PCI Security Risk Assessment to help them maintain, document, and demonstrate compliance in managing credit card payments. By doing so you may avoid the penalties that apply to non-compliance.
As one would expect, the financial services industry is heavily governed by a number of federal and state regulations intended to maintain the integrity of the financial system upon which our entire economy is founded. These include the Gramm-Leach-Bliley Act (GLBA), the Dodd–Frank Wall Street Reform and Consumer Protection Act, and the Federal Financial Institutions Examination Council’s (FFIEC) Cybersecurity Assessment Tool.
As an industry that relies extensively on credit card payment processing, it is also subject to the Payment Card Industry Data Security Standard (PCI-DSS). Also applicable are the Sarbanes-Oxley Act (SOX) and the SSAE 18 standard and System and Organization Controls (SOC) developed by the American Institute of Certified Public Accountants (AICPA).
Sarbanes-Oxley provides stringent rules for accounting and management firms as well as public company boards, and also regulates the accuracy of financial recordings. SOC-SSAE 18 requires service-providing organizations holding data belonging to others to demonstrate they have the necessary controls, policies and procedures in place to ensure customer data privacy. SOC 1, for example, deals with internal controls for financial reporting, and SOC 2 and 3 with trust services.
Healthcare providers, healthcare practices, and healthcare business associates are governed primarily by the Health Insurance Portability and Accountability Act (HIPAA) and the Health Information Technology for Economic and Clinical Health (HITECH) Act. The two are separate and unrelated laws, but they do reinforce each other in certain ways.
HIPAA defines very clearly the parameters of enterprise-wide risk analysis, and the Office For Civil Rights is widely respected for liberally meting out fines and penalties for non-compliance, especially if a data breach occurs in absence of a recent HIPAA Security Risk Assessment. HITECH requires any physician or hospital that attests to Meaningful Use (of electronic health record data) to also have performed a HIPAA Security Risk Assessment as outlined in the Omnibus rule.
Both of these Acts stress compliance as a means of protecting the privacy, security and confidentiality of patient information. Additionally, as most healthcare providers accept credit cards in payment for services, the PCI-DSS also applies.
There are additional compliance requirements for these industries, as well as other industries, including hospitality, media and entertainment, for example. 24By7Security has carefully developed assessment protocols in order to meet the specific requirements of a multitude of industry regulations.
In the ideal world, security risk assessment is a verb denoting an on-going, continuous activity. An organization always knows where their risks reside, what safeguards they currently have in place, and what improvements are underway at any given time. And there are enterprises that meet this highest standard.
Realistically, however, most organizations commission an assessment annually or every few years, once their baseline assessment has been conducted and documented. In the healthcare industry, for example, a HIPAA Security Risk Assessment is recommended as an annual practice, and for some agencies and incentive programs it is a requirement for Meaningful Use attestation.
While HIPAA rules are most often interpreted to require an annual Security Risk Assessment, we have also seen those rules interpreted as ‘regular’ or ‘periodic’ assessment requirements. This generally has to do with the size of the healthcare entity. For example, a large hospital system may be more invested in annual assessment, as opposed to a solo-physician or other small healthcare practice who may not be in the same position or have the same resources.
One thing is certain in any case and in any industry, however. Where mission-critical information systems are in place to collect, process, and store sensitive patient, customer, employee, payroll, or payment data—an annual assessment is just smart business regardless of your industry, size or circumstances.
According to ISACA, a non-profit global organization engaged in promulgating best practices for information systems in all industries, a comprehensive enterprise Security Risk Assessment should be conducted at least once every two years to discover the risks associated with the organization’s information and information systems. For mission-critical information systems, ISACA recommends conducting a Security Risk Assessment more frequently, if not continuously.
New and revised regulations applicable to your specific industry also play a part in suggesting assessment frequency.
And any introduction of a new information system, or extensively updated system, or implementation of any major change, should trigger a Security Risk Assessment within the organization.
At 24By7Security, our fundamental guidance is to conduct at least one Security Risk Assessment as a baseline, so that it is clear where your organization stands at that moment in time with respect to all identified points of risk and vulnerability.
Once your baseline is completed and documented, you will have the flexibility to prioritize an action plan for issues identified as High Risk and Moderate Risk—as your organization is able to assign resources to address them. Generally, most should be addressed within three to four months. It has been our experience that, once an organization has its baseline assessment, it becomes considerably more efficient and compelling to conduct follow-on assessments at appropriate intervals.
Cybercrime is an equal opportunity threat, but cybercriminals tend to exploit the weakest security programs. From their perspectives, why make the effort and spend the time attempting to hack into a database guarded by a solid firewall and intrusion detection and prevention system when right around the cyber corner, so to speak, is an unprotected or poorly protected database?

And there’s the additional consideration of ongoing advancements in cyberthreats and cybercrime, including constantly-evolving social engineering schemes that rely on unwitting employees to open cyber doors. A popular social engineering technique is the phishing scheme, which relies on spoofed emails to trick untrained employees into revealing sensitive information, or paying bogus invoices, for example.
These scams can create chaos within an organization’s financial systems and other information systems—causing serious reputational harm, damaging the brand, eroding customer confidence, and attracting the scrutiny of regulators. And yet they can be avoided with frequent employee training and testing.
We’ve explored the concept of the baseline assessment as an aid to understanding an organization’s vulnerabilities, including what they are and where they are. We’ve reviewed the impact that cybercrime can have on an organization. (Read more about Incident Management.)
Conducting Security Risk Assessments as part of an overall information security program offers some indirect advantages too - advantages which organizations can leverage to strengthen market share, reputation, and profitability. Following are three such benefits:
Building Customer Trust. Customer trust is important in building brand loyalty, which can in turn lead to referrals, new business, and revenue growth. A good cybersecurity program can play a vital role in developing customer trust, and Security Risk Assessments are fundamental to a sound cybersecurity program.
Maintaining Agility. Competing in a digitally-driven economy requires agility. To this end, we continue to update our organizations by adding new technologies, applications and systems. We need to make sure that we build security around these additions in order to maintain our data safeguards, and our ability to compete without incident.
Avoiding Incident Costs. Most organizations do not budget for data breaches or malware attacks. Unexpected expenses, such as system downtime or the theft of intellectual property, to name just two, can severely impact the financial health of a business. By deploying cybersecurity solutions proactively, including regular Security Risk Assessments, these costs can be avoided.
In addition to the obvious benefits described earlier, cybersecurity measures can actually improve your bottom line by delivering indirect advantages to your organization.
The National Institute for Standards and Technology (NIST), an agency of the U.S. Department of Commerce, developed a Cybersecurity Framework that integrates cybersecurity industry standards and best practices to help organizations better understand their cybersecurity risks and manage cybersecurity incidents, such as a data breach, malware, or DDoS attack.
The widely accepted framework is based on five pillars: Identify, Protect, Detect, Respond, and Recover. The underlying questions, outlined below, will assist in determining the overall state of cybersecurity at your organization. So, ask yourself, or your CISO or IT Manager:
The first pillar, Identify, is first for a reason. Without first identifying where an organization is vulnerable to cybercriminal activity and other risks, including internal threats, it is virtually impossible to protect the organization. And the best way to understand risks, where they reside, and how serious they are is to conduct a Security Risk Assessment.
The experienced professionals at 24By7Security bring to each engagement a full complement of expertise and credentials. Contact us for your next Security Risk Assessment or other cybersecurity service or call 844-55-CYBER.
At 24By7Security, Inc. we are your trusted partner in Cybersecurity and compliance. We help you manage your cyber risk programs so that you can focus on your business.
24By7Security, Inc.
4613 N. University Drive, Suite #267
Coral Springs, FL 33067
Toll Free: (844) 55-CYBER
Email: contact@24by7security.com
© 2019 24By7Security, Inc. - (844) 55-CYBER. All Rights Reserved.
Signup for news and special offers!